SSO (single sign-on) now available for cleverQ
We are pleased to introduce a significant innovation at cleverQ: Our users can now benefit from the Single Sign-On (SSO) feature. This advanced authentication method enhances the security of the login process while also simplifying the use of our platform.
What is SSO and how does it work?
SSO allows users to access multiple systems and applications with a single login, offering a significant advantage, particularly in complex IT environments. Authentication is managed by a central Identity Provider (IdP), ensuring secure and seamless access to all connected services.
The process is straightforward: after the initial login, such as through the intranet, an encrypted token is used to grant access to cleverQ—eliminating the need to re-enter login credentials.
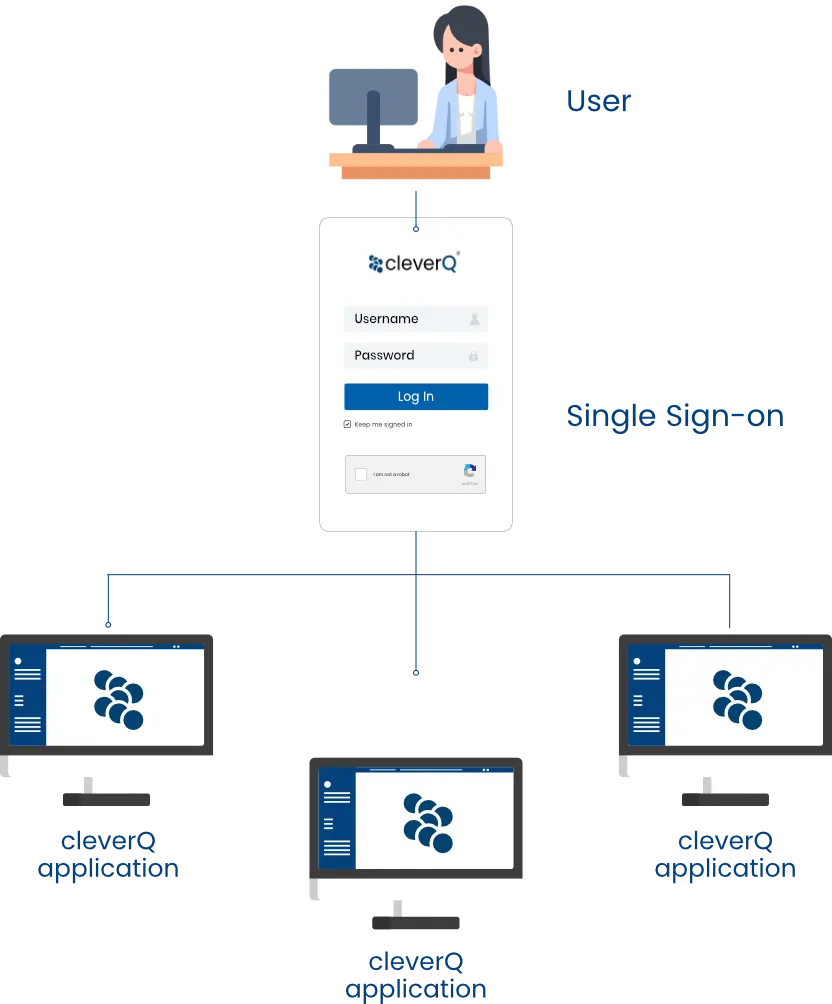
The advantages of SSO with cleverQ
With the introduction of Single Sign-On (SSO), cleverQ adopts a modern authentication method that provides companies with an efficient way to centrally manage access and safeguard sensitive data. Below is an overview of the key advantages:
Improved user experience
SSO eliminates the need to log in multiple times, which can be a significant time saver in the long run.
Improved security
Through centralized authentication with encrypted tokens, SSO minimizes risks such as password theft and phishing. In addition, access can be quickly deactivated centrally in the event of security problems.
Efficient rights management
IT departments can easily manage, centrally assign or revoke access rights - ideal for growing companies and organizations.
SSO and multi-factor authentication (MFA)
For additional security, cleverQ can easily combine SSO with multi-factor authentication. This ensures that only authorized persons have access to sensitive data and functions.
SSO and the EU DORA Directive
The issue of security is also highlighted by the European Digital Operational Resilience Act (DORA). The directive requires companies to proactively manage IT risks. With SSO, you meet important security requirements such as strong authentication and access controls.

